This brief presents a strategic imperative. The development of the IMF is consistently bound by a very complex set of messaging – not just within the MoD but also across its supplier base – whereby interlinking technology, organisational and institutional change is hindering scalability across ‘The Stack’. Increasingly, the three components of technology, people, and change need to be brought together using simple themes of design, build, secure and deliver to create the required capability positioning both within the MoD and its acquisition processes. This will demand a unifying plan/approach by the MoD to manage and exploit fully the IMF approach – consolidating a range of individual components such as cloud, security, et, under a cohesive plan/framework to support operational outcomes.[/note] to embed an Identification/Mission First (IMF) framework at the core of UK Defence. In the face of rising digital threats and rapid technological evolution, the UK must shift from legacy force structures to an agile, information-led defence model where identification, not just firepower, drives operational advantage. IMF is defined as the ability to collect, process, and exploit information faster and more effectively than adversaries, seamlessly connecting Intelligence Surveillance and Reconnaissance (ISR), Logistics (including Medical), Command and Control (C2), and FIRES. This is both a technological and behavioural shift, aligning with modern warfare doctrines such as UK Fusion Doctrine, NATO’s Comprehensive Approach and the Observe, Orientate, Decide, Act (OODA) loop.1
In an increasingly congested, contested, and connected battlespace, information superiority—not platform superiority—is the decisive edge, with speed of identification and mission alignment emerging as critical differentiators. As such, data must be treated as a strategic asset, akin to oil in the 20th century, requiring ethical prioritisation, protection, and operationalisation. Furthermore, civilian digital infrastructure, including social media and undersea cables, forms a crucial part of the intelligence, surveillance, and reconnaissance (ISR) ecosystem, and must be lawfully integrated into defence strategies.2
To operationalise these imperatives, several core recommendations are identified and proposed. Under Leadership and Governance, Defence should appoint a Senior Responsible Owner (SRO) for Identification/Mission First (IMF) and establish a Digital Identification Task Force under Military Strategic Headquarters (MSHQ) to oversee strategy, ethics, and innovation. In terms of Workforce and Skills, it is essential to build a pipeline of data-literate, ethics-conscious strategists, and to incentivise digital fluency across all services through tailored career pathways. Regarding Investment and Architecture, Defence must prioritise sovereign, interoperable digital systems with low latency and secure data exchange, while embedding real-time, multi-domain identification layers into command, control (C2), and ISR platforms.
For Operational Integration, IMF capabilities should be embedded into Joint Action doctrine and field exercises, and open-source intelligence should be harnessed through structured, policy-governed approaches. Finally, under Strategic Communication and Ethics, a Defence-wide Digital Ethics and Law Compliance Framework must be established, alongside clearly defined red lines for the use of private and civilian digital systems in targeting and surveillance. These measures collectively aim to ensure that Defence maintains its competitive edge through agile, ethical, and integrated information dominance
Introduction
Digital connectivity and rapid technological change have redefined modern warfare, where information superiority increasingly determines success. While kinetic force retains importance, digital tempo—the speed and effectiveness of information-action cycles—has become decisive.3
The MoD remains constrained by legacy structures and cultural inertia. This brief advocates embedding IMF as a core organising principle for capability development, grounded in both theory and practical examples.
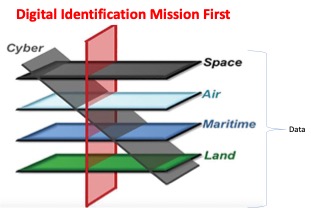
Figure 1 above articulates the ‘digital stack’4 in which IMF operates and explicitly refers to the integrated ecosystem linking platforms, sensors, users, networks, and command structures. This system enables near-real-time ISR, fire support, logistics coordination, and decision-making. These combinations are curating experiences in the digital environment for users (civilian and military). This consists of combined layers of digital capabilities that in turn provide the human-computer interface which includes platforms (ships, planes, tanks, people et al) sensors, digital cellular and communications networks, internet gateways (subsea cables, landing points satellite systems5) and geospatial resource, value and supply chains. This is increasingly linking business and warfighters into both physical and digital processes to derive effects or value (products, services and kill chain) For example in 2011 during the UK/French campaign a key lesson identified was the use of by the military of social media to observe how strike confirmations could be reviewed within minutes of the activity as Libyans who were opposed to Col Gaddafi organised themselves via social media to provide NATO with locations of Libyan Force elements . This ‘democratization’ of the intelligence and targeting cycle with citizens providing an ‘Intelligence, Surveillance and Reconnaissance (ISR) as a service’ on the ground, identifying targets and providing confirmatory evidence of how successful the NATO attack had been, pointed toward a new future in how warfare would be conducted in the Contemporary Operating Environment – whereby the citizen via the digital function would become an element of the military sensor array and a component of fighting power for force elements. By 2016 UKs involvement in Syria (Op SHADER) reinforced this development, as has the Russian invasion of Ukraine in 2022. Whereby the military kill chain did not necessarily have to rely upon military surveillance to achieve outcomes – they could draw upon a ‘stack’ of digital resources who were watching what was happening in real time around them. This has consequential effects for the military which are explored below.
The examples from Libya (2011), Syria (2016), and Ukraine (2022) illustrate how open-source intelligence and civilian digital participation reshape the ISR landscape, and as such this has consequences for UK MoD particularly with respect to force design and force development and incorporating open-source ISR into UK doctrine responsibly and ethically.
Identification/Mission First Defined
IMF is the seamless integration of identification, information exploitation, and mission execution. It links ISR, C2, logistics, fires, and protection through a digitally enabled, behaviorally informed framework. This approach aligns with the OODA loop and UKs Fusion Doctrine and NATO’s Comprehensive Approach, accelerating tempo while ensuring strategic coherence.6 It is not merely a technological concept—it is behavioural, organisational, and strategic. In the context of modern military operations, Identification/Mission First acts as the connective tissue across mission threads such as Fires, Logistics, ISR, and Force Protection. Without Identification/Mission First framework, there can be no effective Joint Action. Without Joint Identification/Mission First Manoeuvre, there is no digital advantage. This triad must form the foundation of UK Defence thinking moving forward. See Figure 2 below.7
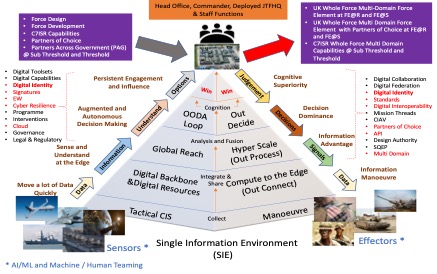
Strategic Context
The UK faces a series of overlapping challenges: the re-emergence of great power competition, austerity-driven capability gaps, the rise of information-led hybrid threats, and the rapid proliferation of advanced technologies. The 2025 Strategic Defence Review acknowledged these issues but failed to provide a cohesive Identification/Mission First delivery framework. As a result, adversaries are gaining ground, particularly in the digital / cyber, space, and grey-zone operations.
Lessons from Industry and the 4th Industrial Revolution
The commercial world has already embraced the information age. Companies like Google and Facebook monetise user behaviour through data extraction, analysis, and predictive modelling. This behavioural data has replaced natural resources as the primary raw material in the digital economy. By contrast, the MoD has lagged. The MoD must adopt an identification/mission first approach, treating data and digital identification as strategic assets, not administrative burdens. As such MoD must commence the journey and treat data as strategic capital. Defence must also similarly value data and identification not as overhead but as core capabilities. However, the ethical and legal implications of leveraging civilian digital infrastructure must be addressed via policy and oversight aligned with UK and international law.
Organisational Inertia and the Cost of Delay
The UK’s defence acquisition system remains slow, stove-piped, and focused on legacy concepts of war. This has led to systemic failures in delivering capabilities aligned with operational needs. Two major cultural dynamics exacerbate this: metrics over outcomes, and risk aversion. The dissonance between operations and headquarters has led to inefficiencies and reduced combat effectiveness.
Reform must address a metrics-over-outcomes culture and institutional risk aversion. Performance incentives should align with mission outcomes, not compliance checklists.
Recommendations
The following recommendations are made:
- Leadership and Governance: Establish an SRO for Identification/Mission First and build a SQEP team
2. Workforce Transformation: Train and retain identification professionals.
3. Digital Investment: Focus on data-first approaches.
4. Collaboration: Integrate identification/mission first efforts with allies and government.
5. Operational Integration: Embed mission threads.
6. Strategic Communication: Strengthen InfoOps.
Vision for Integrated Force 30
To achieve the desires outlined in Strategic Defence Review 25 and its supporting military component – Integrated Force 30, the UK Defence landscape must be underpinned by sovereign, secure identification capabilities, cyber resilience, and digitally integrated mission planning. This transformation must be ethical, legally compliant, and adaptive to Artificial Intelligence (AI), quantum, and cognitive warfare challenges. This future enables assured mission success in a congested information battlespace. See Figure 3 below.
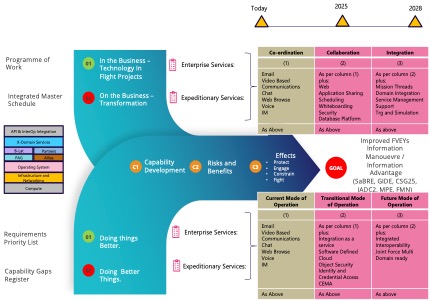
Conclusion
IMF is not a slogan but a strategic imperative. To maintain relevance, UK Defence must adopt digitally coherent command structures that are fast, ethical, and resilient. The MoD must act urgently, decisively, and strategically to implement this transformation at scale. The contemporary operating environment demands a Defence organisation that can think and act digitally. Identification/Mission First is the foundation of modern combat power and national resilience. The MoD must now act with urgency and commitment.
Howard Tweedie
Howard Tweedie TD, CEng, FBCS, CIPT, FIAP, MInstRE is a seasoned defence and technology practitioner with operational and commercial experience. The views presented are personal and do not represent the UK Ministry of Defence.
Footnotes
- The OODA loop is a decision-making model consisting of four steps: Observe, Orient, Decide and Act. Developed by Col John Boyd, it helps individuals and organisations make effective decisions in a competitive and rapidly changing environment by continuously cycling through the stages.
- Gartner, in its Strategic Global Trends for 2025, has identified disinformation security as an emerging threat vector facing all organisations. This growing concern stems from the actions of threat actors who exploit social media and fake news to manipulate public and private opinion at critical moments. Tactics include deepfake attacks that compromise biometric authentication—a foundational component of the technology stack—and the deliberate crafting of harmful narratives. These narratives are increasingly amplified through the misuse of artificial intelligence, which is being weaponized to damage reputations, perpetrate fraud, challenge governmental narratives, undermine commercial brands, and manipulate global digital audiences
- The emerging digital fabric for warfare exemplifies misinformation, dis-information, and mal-information. These elements now constitute some of the core elements of the information framework, which plays a dominant role in the information warfare domain. These components are key enablers of grey zone operations and form an integral part of the hybrid warfare toolkit employed by current adversaries and strategic competitors. Dis-information, particularly when combined with influence operations, is a critical factor within hybrid warfare—both as a threat and in the context of building national and organisational resilience.
- See Combined Information Overlay for Situational Awareness in the Digital-Anthropological Terrain: Reclaiming Information for the Warfighter – Cyber Defence review Vol 6, (2021) No3 pp96-99. By Zachery Rogers and Emily Bienvenue.
- With over 60% for the global market for satellite infrastructure being provided by the commercial sector, The European union Agency for Cybersecurity (ENSIA) recently published Space threat Landscape Report (Mar 25) indicated the strategic importance of satellite communications toward the global economy and wider societal functions including but not exclusively relating to areas such as telecommunications, navigations systems and more importantly emergency response, agriculture and supply chain for interdependent economic and business services.
- Across platforms sensors, people (including Non-Personal Entities) and locations
- Ukraine’s Lessons identified are adapting the OODA Loop. The conflict has highlighted the following key aspects to the processes which include: Real-Time Intelligence: Ukraine has effectively utilized open-source intelligence and real-time data to inform its military strategies, demonstrating the practical application of the OODA Loop in a digital age; Cyber Defense: The war has also showcased Ukraine’s capabilities in cyber defense, emphasizing the need for a robust OODA Loop that incorporates cyber operations alongside traditional military tactics and Autonomous Systems: The use of drones and other autonomous systems in Ukraine illustrates how modern warfare is increasingly reliant on technology, necessitating an evolution of the OODA Loop to integrate these new tools effectively.

