Synopsis: To execute contemporary warfare more efficiently, to weaponise data at an industrial scale and to deploy a full-spectrum of information manoeuvre weapons, defence needs to deploy modern hyper-scale computing platforms on today’s battlefield. In doing so it will attract innovative young soldiers to develop and exercise processes, applications and toolsets that will solve the future military problems we have not yet envisioned. Welcome to virtual war.
This article originally appeared in the Summer 2019 Royal Signals Journal. A shorter introduction to the subject can be found in the Short Reads section.
Today’s Virtual Battlefield
‘The nature of persistent state-on-state competition continues to challenge traditional, linear crisis response command and control processes and structures. Defence, therefore, requires an applied operating concept, doctrine and new approaches to reflect a multi-domain, full-spectrum approach.’1
The contemporary explosion in computing power, the paradigm shifts in social communications and rapid socio-economic changes affecting today’s global society are disrupting our traditional military construct. They are transforming the traditional linear battlefields into the new multi-domain Congested, Cluttered, Contested and Constrained virtual battlespaces.2 In this strategic competition beyond war or peace, a ‘smart’ military must be capable of deploying an array of technical enabling toolsets and technical weapons systems, build competencies in its people and develop a 21st Century Information Age CONOPS that will aggressively deny, shape and dominate the virtual battlefield. To defend, prevail and thwart the incoming ‘Cyber Blitzkrieg’ we need to now enable a full spectrum of defense, influence and information dominance capabilities across all battle space domains.
Today’s Multi-Domain BattleSpace – Congested, Cluttered, Contested and Constrained
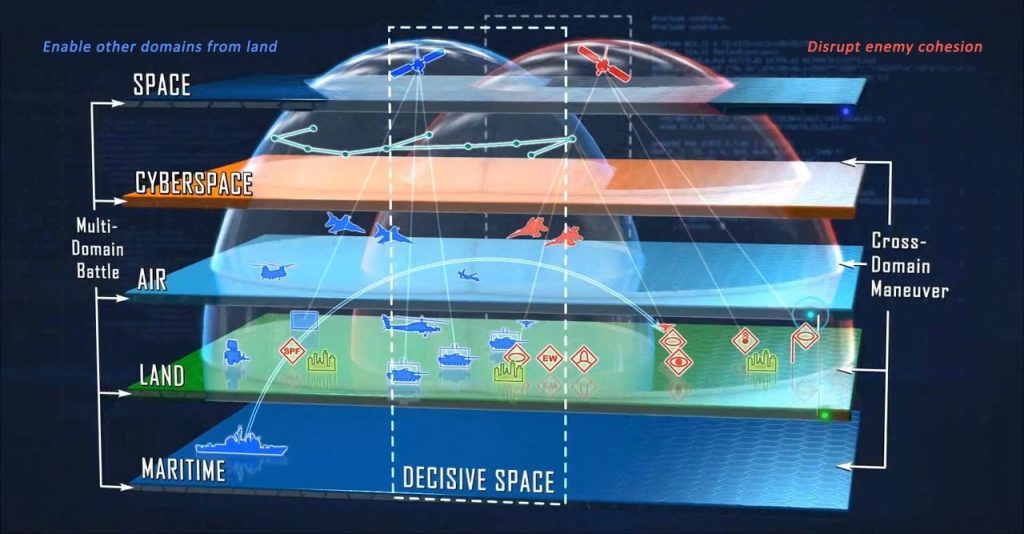
The character of warfare in this multi-domain battlespace has also changed (as demonstrated in the case of Ukraine, Georgia, and Estonia): A new 4th generation hybrid warfare, a grey proxy style of virtual conflict is blending all past generations of physical warfare with today’s contemporary technologies. This hybrid pseudo-war is playing on society’s omni-reliance nay addiction to instantaneous data feeds from its all-pervasive social networks. The next generation of information tools, influencing physiology and interoperable weapon systems now require a new emergent Virtual Warfare operating doctrine enabled by modern hyper-scale computing fabrics.
‘These technologies will fundamentally reshape the character of war, if not – as some have speculated – its very nature’ – Prof Risa Brooks, USMA Westpoint.4. (2018) War on the Rocks: Technology and future war will test US civil-military relations[/note].
Providing such an infrastructure fabric enables the commander to execute contemporary warfare more efficiently, weaponise data at an industrial scale speedily and deploy a full-spectrum of information manoeuvre weapons. It enables a sway of instruments, sensors and cameras at the battlefield edge thus freeing up thousands of highly trained soldiers to be deployed more appropriately. It enables hundreds of a new supporting application from logistics to planning, from Battlefield Management to Combat Net Radio (CNR) allowing HQ staff to consider, plan and execute more effectively. It enables integration with supporting applications on NATO’s Federated Mission Networks as well as other partner applications permitting better interoperability. It will enable HQs to receive, analyse and comprehend data feeds from all these endpoints delivering more accurate and more effective decision making. It enables Sentiment Analytics of Open Source Intelligence (OSINT)/Operational Intelligence (OPINT) and the prosecution of defensive and offensive Cyber operations to protect our own forces and disrupt our adversaries.
By providing these Information Manoeuvre options to the commander, Information Advantage is obtained allowing the multi-domain commander to dominate the Cyberspace battlefield layer and provide Information Supremacy. The asymmetric competitive advantage and force-multiplier effect of a small, suitable equipped and suitable trained offensive Information Warfare unit executing Virtual Warfare doctrine on a suitably connected technical platform, will deliver a physical effect in all domains completely disproportionate to its size, thus ‘ameliorating many of the shortcomings of a reducing number of platforms and people – Gen Barrons.’5
For all of this to be realised, it will require the creative integration of tech sector product roadmaps, soldier competency development aligned to the Skills for the Information Age (SFIA) framework and a new Information Age doctrine adopted from the tech sector’s best practice and applied to today’s battlespace. Welcome to the next war.6
Virtual Warfare Principles
The conduct of Virtual Warfare and virtual operations will require a set of rules and guidelines that represent the embodiment of conflict from a digital perspective. The following principles could be used to prosecute the virtual war, in conjunction with the conventional principles of war:
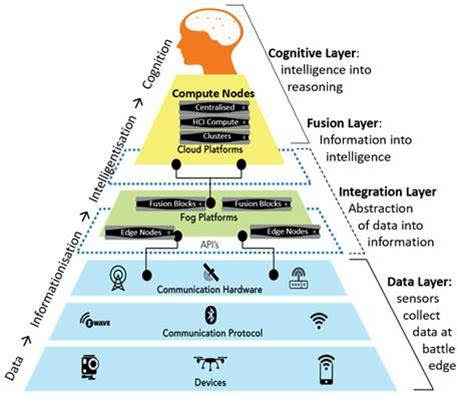
Informationisation: Everything will be digitised into data, collected, transported, stored and processed into information.
Intelligentisation: Information will be analysed into intelligence.
Cognitivism: Sense will be made of intelligence to enable (and automate) decisions and actions.
“We will focus on gaining ‘Information Advantage’ as the character of warfare changes. The effective collection, analysis and dissemination of vast qualities of data will enable us to understand how our adversaries are thinking, how they will act against us and how we can deter or defeat them.’7
Informationisation: In virtual war, the commander has access to thousands of digital endpoints at the battlefield edge, delivering a torrent of data from a multi-networked array of instruments, sensors and cameras giving Operational Situational Awareness. Also available is the tsunami of data from social media and other Open Source Intelligence (OSINT) essential for real-world sentiment analysis and Contextual Situation Awareness.
At the same time, our adversaries in recent years (as demonstrated in the wars in Ukraine, Georgia, and Estonia), have fully developed and perfected their Virtual Warfare CONOPS i.e. Gerasimov’s ‘New Generation Warfare’ doctrine.8 They have digitised their world, processing similar data feeds coming from their perspective of our BattleSpace and studied how to disrupt and ossify our forces with confusion and chaos. As defined in the PLA’s Systems Destruction Warfare doctrine their mission is to exploit, disrupt, confuse and make us doubt our own data feeds in our global Systems-of-Systems battlespace topology (Figure 2).9, The resultant carefully choreographed chaos, a ‘Black Mist’ of psychological disorientation and ambiguity, will make our forces impotent, creating time and space for their more decisive actions.
A System-of-Systems – The Multi-dimensional modern BattleSpace

Intelligentisation is the application of modern technologies to add sense to data and information. To fight at pace in the virtual domain, a ‘smart’ military needs to use advanced digital compute platforms that employ Big Data analytics, Visualisation and Artificial Intelligence (AI) applications to process all the data held in a shared data-warehouse to evidence and improve battlefield decision-making. A ‘smart’ military will ‘deliver and manage agile digital data feeds and services across application, network and infrastructure platforms; protect data feeds/information and at the same time exploit/disrupt adversaries; and advise commanders on the use of all these data feeds and information capabilities.11
There are still technical challenges
to be overcome. To deliver the effects required and at the pace will require a
secure, high capacity transmission fabric to transport any data on demand, a
federated multi-cloud, multi-tenanted hyper-converged compute platform, and the
agile integration of applications using this infrastructure to store, analyse
and visualise data in real-time.
“We’re drowning in information and starving for knowledge.” Mark Twain
Cognitive Manoeuvre: It is now widely recognised that in the Virtual Warfare speed will trump accuracy and speed will be the new measure of success. Thus, if a commander can just ask an AI web-bot like Alexa™ to search, analyse and deliver a live information product from the global data-sphere in nanoseconds, then the future value of military information services needs to be re imagined.
‘Defence has a plethora of high-quality intelligence analysts but is it ready to exchange two-thirds of them for data scientists?12
The live processing of the torrent of OSINT/OPINT and integration with a myriad of other data feeds using AI algorithms to weaponise it in a Distributed Digital Infrastructure (DDI) is highly likely to be the primary role of the Joint Signals (J6) function in a Virtual War.13 To provide context, background and understanding in this lattice, in order to support better evidence-based decision-making in the cognitive environment, in the context of a live, dynamic and confused battlespace will be the role of Joint Intelligence (J2).
Air Vice Marshall Johnny Stringer, JLF CoS summarised it recently as ‘…the need to understand and fuse this open-source intelligence with other feeds will place increasing demand on automation and big data analytics: without this, we risk generating even more ‘Collect’ of raw data without the means to ‘Process & Disseminate’ refined and timely intelligence product’.14
The intelligence analyst’s role in Virtual Warfare will likely change to that of a storyteller of the actual reality devoid of nuance or ambiguity in a coherent manner that commanders understand and internalise. Intelligence operators will need to work closely with IT platform operators to translate, interpret and fuse the data feeds into intelligence product, then articulate the aesthetics of what is happening all around the multi-dimensional, multi-domain battlespace including the implications on the commander’s options. This understanding relies on the transport and fidelity of the data feeds into these AI algorithms and the correct visualisation of the analysis to deliver accurate intelligence output (Garbage in, Garbage out). To stay agile, relevant and dominant in the Virtual War, J2/J6 need to provide a sense-making cognitive service for commanders based on accurate data analytics but interpreted and contextualised by a human analyst.
Virtual War Conops
The tactical playbook for warfighting has been constantly updated over millennia. Virtual Warfare is no different: There are principles, concepts and tactics to be developed.
“…for the millionth time, it is not about technology: It is about the integration of operational concepts and organisational constructs that will shape the way we integrate and use the technology.”15
These operating principles, equipment, services and the talent/leadership required to operate them are detailed in ‘On Virtual Warfare’ in the Royal Signals Journal (Summer 2019) <Click Here>.
Virtual Warfare Operating Platforms
Despite claims from the Signals fraternity, Virtual Warfare is not actually magic, it needs physical operating platforms and trained people, similar to conventional warfare. From these platforms, a commander can conduct information manoeuvre, strikes and prosecute both offensive/defensive joint tactical information operations in order to deliver Information Advantage thus dominating both the Virtual and Physical Battlefield. This new emergent Virtual Warfare CONOPS will need to be enabled by a hyper-connected grid of modern Hyper-Converged Infrastructure (HCI) platforms, scaled to deliver this power at an industrial scale. This allows the commander to execute both global multi-domain contemporary warfare more efficiently and deploy the full-spectrum of information manoeuvre weapons at pace.
This distributed computational power will be needed to enable future military forces to receive, analyse and comprehend contemporary battlespace data feeds in real-time. This will be achieved by integrating Commerical Off The Shelf ICT, technical competencies frameworks for operators and the experience/innovation/energy of creative young soldiers with Information Age strategies from the commercial sector to form the new ‘British Way of War and Theory of Winning’.16
The resultant secure multi-cloud computer architecture when connected and deployed in a Virtual Warfare scenario, would enable J6 planners to push enterprise compute power out to all edges of the battlefield, unify soldiers, devices and compute power into one single enabled force – the ultimate force-multiplier.
Future Battlefield Computing Infrastructure & Networking Topology
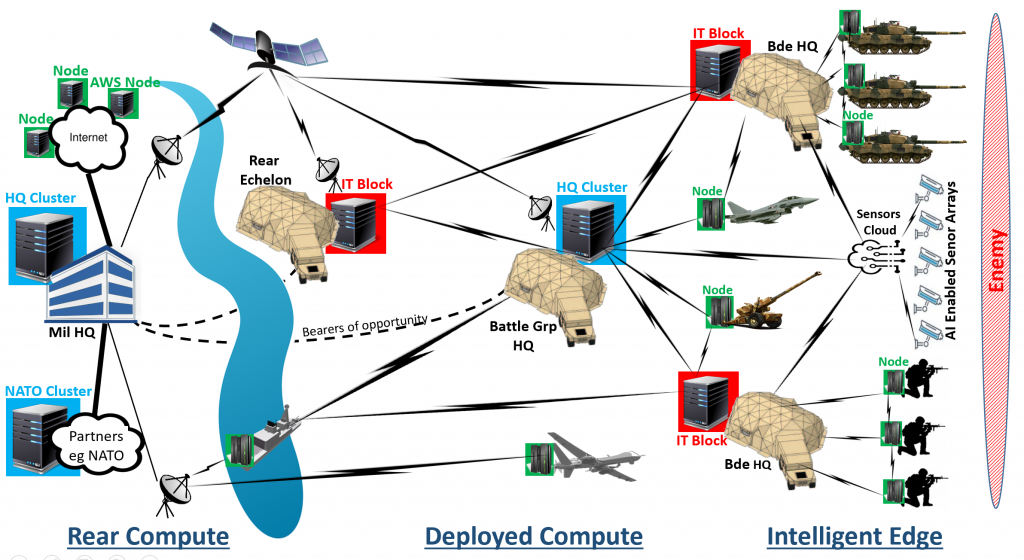
Figure 4 A Distributed Digital Infrastructure (DDI) topology
By integrating with and leveraging other private clouds of resources from partners, applications such as NATO’s Federated Mission Network planning or logistics apps can be incorporated and deployed.17 By leveraging other public clouds, solutions can be processed on public computers e.g. on AWS Cloud for Sentiment Analytics of OSINT. The Army’s own internal platforms can then be used to deliver mission-specific applications e.g. BattleSpace Combat Management Systems (BCMS) or Software Defined Combat Network Radio (SD-CNR) services inside a secure cloud. Overall the benefits of using DDI (Figure 4) is that it will improve the end-user experience, provide a stronger lattice of integration/service continuity across networks, reduce latency, allow geo-diversity, stiffen data protection and ensure sovereign data compliance.
Conclusion
The implications for defence are enormous. Because computing power is now virtually unlimited and the price so low, its use in virtual and contemporary warfare theatres has to be totally re-imagined. With this power, we need to re imagine how we achieve military superiority in both the virtual and physical battlespaces, defend this architecture and protect our data.18 At the same time, we need to imagine how we would disrupt and exploit our adversaries’ data. We need to imagine how would we dominate this vital ground, similar to what our adversaries are already planning to do to us.
The Technology Stack
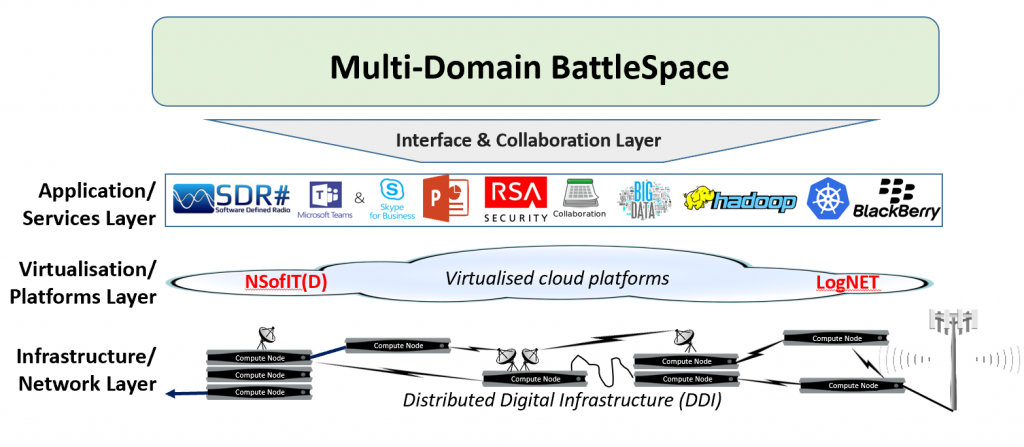
Failure to deploy, experiment, train and exercise manoeuvre with this Technology Stack (Figure 5) will leave us with an inability to advise the commander on the use of their information capabilities, leading to a failure of the commander to deliver physical and information superiority on the battlefield.
Glossary
What is Hyper-Converged Infrastructure (HCI)?
In the early 2000s specialist software called Virtualisation was used to Converge computer equipment. It linked all the separate computer chips, memory and disks to form logical Virtual Machines (VMs). In 2012 the concept was perfected leading to Hyper-Converged Infrastructure (HCI) which totally re-architected, simplified and commoditised data-centres into boxes no bigger than a large briefcase. As the same time, revolutionary advances in the performance of computer chips, disk-storage and networking mean that today, a single HCI ‘node’ has enough computational power to easily run all the applications and services needed by a Battle Group HQ. With the inclusion of flash memory, Solid-State storage Drives (SSD), parallel addressable memory chips and fibre interconnect networking, these nodes can be miniaturised and integrated into ‘blocks’ to provide computers so powerful that could each run a small city. When these computer ‘blocks’ are stacked (like Lego™) to form a ‘cluster’, they work as one homogeneous computer to provide previously unimaginable computing power and storage capacity.
So What?
Today a Virtual Warfare commander can have virtually limitless computing power in his tent. The question now for the military is to imagine how they can use the power of this weapon to deliver battle-winning applications and services that enable the commander to dominate both the information and physical domains.
What is a Distributed Digital Infrastructure (DDI)?
This is computer architecture description that describes a mesh of computing power when linked together to form a single system-of-systems. It is sometimes described as ‘grid’ computing where various nodes (servers) are connected together by various network links in a lattice topology. This Peer-to-Peer type network uses special control software embedded in each node to give the impression that each user has the whole network resources available (a pseudo-private version of the Internet).
So What?
One of the advantages of this type of networks is it all works autonomously, automatically handling failures in a node, is self-healing if a fault occurs and instantaneously switches to backup nodes if the primary controller node is destroyed. The science was originally designed for a nuclear era military but then commercialized and hyper-scaled to deliver omnipotent services from Google, Facebook and Amazon. It is this architecture that underpins modern cloud services like Uber, Airbnb and Netflix. When this cloud architecture is deployed in a Virtual Warfare scenario, it would enable military planners to push enterprise compute power out to all edges of the battlefield, unifying soldiers, devices and compute power into one single enabled force.

Martin Crilly
Martin Crilly is the Chief Architect & Engineering Authority to BAE Systems in the Middle East, and a Reserve Signals Officer. His background is in contempary ICT architecture, technology strategy, cyber-security, J2 and J6 with previous roles in BFC, ISS Ops Plans, GOSCC, DE&S Maritime and others. For more information and articles on Virtual War and similar topics, ‘follow’ him on Defence Connect.
Footnotes
- Joint Concept Note 2/17, Future of Command and Control
- For a modern military to compete and have relevance in this Multi-Domain Battlespace (Figure 1), in ‘the grey zone just below the threshold of conventional warfare’ it needs to replace its 20th Century Industrial Age CONOPS to be capable of joint action in this new hyper-connected pseudo-war.[note[General Nick Carter, Annual Chief of Defence Staff Annual Lecture January 2018
- The Changing Character of Future Warfare Available at https://www.youtube.com/watch?v=0VsikOe_-wg
- Brooks, Risa Professor
- General Richard Barrons, Warfare in the Information Age (2016) https://www.youtube.com/watch?v=m1Ng98RVTcY
- SFIA version 7: https://www.sfia-online.org/en
- Mobilising, Modernising & Transforming Defence Programme Report (Jan 2019)
- battles-cyberwarfare-russia/
- Engstrom, Jeffrey (2018) “Systems Confrontation and Systems Destruction Warfare, How the Chinese People’s Liberation Army Seeks to Wage Modern Warfare”, RAND 2018
- US Joint Chiefs of Staff, 2011a, p. Figure IV-2
- Pope, Lt Gen N.A.W (2018), Master of Signals Intent for the future.
- Jon Rigby, (ex Director of Cyber, Intelligence and Information Integration (DCI3)) & Rob Jones (ex Army HQ) & Ross Baily (ex RAF Intelligence) (2018), A question 4 moment – A perspective on changes to the challenges and imperatives within the SIE, Leidos 2018.
- https://www.computer.org/publications/tech-news/data-center-insider/how-to-manage-todays-hybrid-it-infrastructure.
- Stringer, Johnny Air-Vice Marshal (2018) Change Character, Changing Context, Enhancing Airpower employment in the RAF 2nd Century, RUSI Journal 163:3, p34-42
- Bob Work, US Deputy Secretary of Defence, Washington, Remarks to the Association of the U.S. Army Annual Convention (2016)
- General Mark Carleton-Smith, 2019. https://www.linkedin.com/pulse/new-british-way-war-arnel-david/
- ikipedia.org/wiki/Federated_Mission_Networking
- Defendable Architectures: Achieving Cyber Security by designing intelligence driven defence, Lockheed Martin Corp (2019)





