Winning Decision Superiority and Cognitive Dominance of the next war.
Post-digital has yet to be defined: Some suggest it is would be more accurate to call it the aera of persistent-digital, a time in which we just assume everything has become digital, a pervasive, persistent epoch, simultaneously transformative yet equally irrelevant. Similar to the era of electricity or mains water, this will be the time when digital has become a utility and nothing to marvel at. This will be a time inhabited by digital natives, with digital being a vast homogeneous background commodity, noticed only by its absence. I’ve met one of these digital natives, my 4-year-old granddaughter. As a digital-native she just expects ‘Peppa Pig’ to be on permanent stream to her tablet, instinctively side-swipes my TV to ‘next video’ and has pronounced my land-line phone broken as she cannot see the video of the caller. She has no concept of a pre-digital world, of crackly voices and getting the WiFi to work, nor does she marvel at the amazing capabilities of her tablet, she just expects on-demand ‘Peppa Pig’ is the reality, anything less is a failure.
Despite 30 years in MilTech, I am now starting to follow the lead of this 4-year-old, not trying to define or comprehend the post-digital age, just like her accepting it is already here. Similar to our understanding of vaccines, electricity and mains water, we don’t marvel at the development, generation or transport of these, we just welcome our jabs, make a refreshing cuppa with fresh clean water and watch a boxset powered by perfectly regulated power. In doing so we have moved our thinking away from marvelling at how the technology works and focus on the important question What:
What are all the wonderful innovations we could develop with this commodity, and how would this help win the next war?
Post-digital age
This post-digital phenomenon is identical in all global societies and the implications for ‘Warfare’ and its C2 are chilling. Questions such as how will a weakened state, pseudo-state or next wave of dispersed virtual youth tribe, influence, compete and conflict during this age? What will be involved in the new acrimonious global competition using new forms of non-state violence between philosophies, ideas and economies including in extremis, war. Defining the next war is the challenge, not the flashy kit and technological marvels that have so cunningly seduced us as past years. The current trauma being faced by global militaries grappling with incremental digital change e.g. JADC2, chasing the roller-coaster of seductive novel digital micro-modernisations to achieve fleeting Information Advantage has run its course. I am not convinced this will provide the winning long-term strategy for large, conservative instruments of state power. We carry 100s of years of baggage, rules, processes and industrial-age anachronisms – If only we could see the world through the eyes of a 4-year-old. In this way we would just accept things as they are now, not shoehorn our thinking based on what we have read or have experienced in our old industrial wars; they are not the predictors of the post-digital war.
As digital increasingly pervades, metastasises and saturates our battlefields, processing data up the cognitive hierarchy into intelligence, then into understanding and options with require hard decisions to be made at unimaginable speed by military personnel (see Figure 1). In these increasing cognitive wars, who or maybe what is it we need to provide decision superiority and thus C2 of these lightning engagements.
Post-digital OODA loop
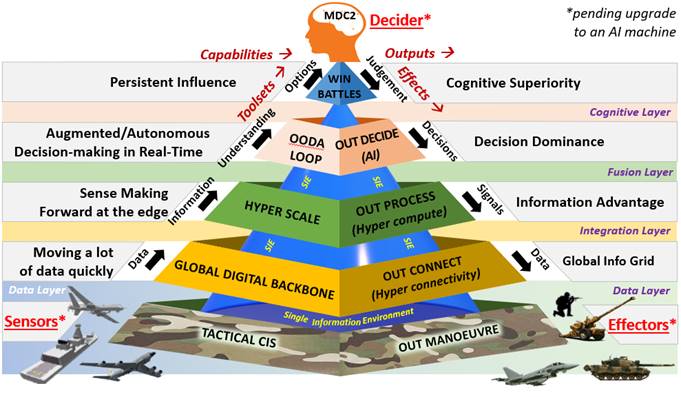 We need now to pause, think and imagine a world where we assume and expect that wars in this post-digital age are going to be technically complex, involve massive amounts of data with new hyper-connectivity multi-channel and media transmission challenges and where constant flux will be the default. Now let’s build, train and work out how we want to fight that war, including the ConOps and C2 of it. Once we have the military blueprints of that engagement, competition or conflict i.e. the post-digital military warfare doctrine, planning and TTPs, only then can we ask our IT supply chain to create the tools to enable us to fight it. Military people decide how to fight wars, not the IT people, so we military people need to dominate and own this new post-digital battlefield.
We need now to pause, think and imagine a world where we assume and expect that wars in this post-digital age are going to be technically complex, involve massive amounts of data with new hyper-connectivity multi-channel and media transmission challenges and where constant flux will be the default. Now let’s build, train and work out how we want to fight that war, including the ConOps and C2 of it. Once we have the military blueprints of that engagement, competition or conflict i.e. the post-digital military warfare doctrine, planning and TTPs, only then can we ask our IT supply chain to create the tools to enable us to fight it. Military people decide how to fight wars, not the IT people, so we military people need to dominate and own this new post-digital battlefield.
How we want to fight in the future is a question for war-fighters…not IT people”
Post-digital C4ISR
C4I: In today’s Informationised battlefield using many of our current C4I capabilities has been compared to the confidence displayed by Captain Grenfell of the 9th (Queen’s Royal) Lancers at the Battle of Mons. As he rode forward in his courageous but doomed Cavalry charge against the Industrial-age German machine guns his confidence with his lance weapon system never waned – “Death or Glory” the battle cry. 100 years later as we send their modern incarnation, the Royal Lancers armoured recce charging forth into the network-centric, cyber, psychological, electromagnetic and hybrid information battlefield our confidence in their current C4I weapon systems may also be equally courageous but doomed. In the post-digital war, we need to immerse into, shape and dominate this new post-digital age battlespace, then find/apply the contemporary technology appropriate to own this battlespace. In doing so now we give our forces far more than information advantage (that has to be expected), we give them decision superiority and cognitive dominance over the brains of the protagonists, the 21st increasingly intellectual battlespace.
ISTAR: Similar to C4I, the production of Intelligence from Surveillance, Reconnaissance and Target Acquisition from the sprawl of battlespace sensors and effectors is essential. But the sequential Korean War era OODA loop ‘kill-chain’concept of Colonel Boyd is no longer adequate in a post-digital war. The complexity, convergence and speed that require a transition to a ‘kill-web’, to handle an inbound hypersonic missile, polymorphic code insertion or social engineering attack are best left to contemporary autonomous systems – the person-in-loop needs to go, he (and she) is just too slow. The post-digital accelerating tempo of war will require ISTAR to be autonomous with control and decision deputized to artificial Intelligence bots who can instantaneously sense, predict then prosecute any target. The milli-second latency times currently being discussed for this cycle/loop mean the benchmark figure for this task is now sub one second.
Future C4I & C4ISR: In the post-digital era, C4I will continue to be the main foundational tenants of future C2 but the technologies used in it will bear no relation to current architectures nor will the current doctrine provide much direction. The current use of Hyper-Converged Infrastructure (HCI) will increasingly provide Hyper-Scaling of compute power (like computer Lego bricks), hyper-connected across a digital backbone forward to the edge of the battlefield into the foxhole and will be a game-changer when deployed. As Quantum or Quantum-like chipsets come online the processing power available will be unimaginable – so let’s start imagining now what we could do with that. The future transmission features of 5G, then 6G (2029) and 7G (2035), BIoT and fibre backhaul capabilities are now being rolled out – What capabilities can we imagine for a military utilising these bearers? How will the enemy use it and how will we defend against their use of it? C4I will mature and morph into new capabilities whos’ character and use will be drastically different from today.
Enabling post-digital C2
The nature of C2, the making of hard decisions and the focus on achieving the mission has not changed; But its character, complexity and speed now require war to be prosecuted warfare in a timeframe of hours, minutes and seconds. Latency, data overload and security are the new enemies, not Russia or China (they have these same problems). Speed of relevancy is our nemesis and the ability to communicate our ideas, messages and effects (before others do) are our new weapon systems. In these post-digital acrimonious global competitions, our soldiers/officers need to move past traditional C4I into an age where they just expect to apply disruptive technologies at lightning speed to handle any mission. Like my granddaughter, they too will assume and expect that everything is already digital, pervasive and persistent, a vast homogeneous secure background utility that they have accepted and are comfortable in (think like a 4-year-old). To enable, compete and win this competition including in extremis war, will demand of them increasingly challenging strain and tests of their cerebral, not physical fitness. As these new technologies, processes and systems start to enable future C2 in this post-digital age, other new enablers and new disciplines, activities and TTP will be developed.
C5I & C5ISR: Cyber somehow has got confused and categorised as a domain of war, it is not: It is a flexible, multi-domain operating construct operating across the 4 physical domains. When reoriented to view it in this perspective, it allows ‘Secure by design’ principles to be incorporated into the foundational architecture of military systems. Defensive Cyber-Security in the protective perimeter fence incorporated into and around military C4I solutions to protect them from breaches of their technological integrity. Defend forward, defence-in-depth or cyber-patrolling is an aggressive military tactic but similar to physical combat it could be considered as Offensive Cyber Operations designed to manipulate, weaken or destroy an adversary’s C4I system and probably an act of war. Similar to Nuclear War, Cyberwarfare is equally as complex, fraught and the cyber wind can equally blow-back on our troops.
C6I & C6ISR: Combat Systems are the software solutions that make the C2 framework work. Whether it is a basic Battlefield Management System (BMS) or an advanced system like JADC2, soldier based apps or an integrated Command & Decision (C&D) systems like the Aegis Combat System, the use of software and in particular App Foundries has and will continue to be one of the biggest growth areas in the post-digital world.
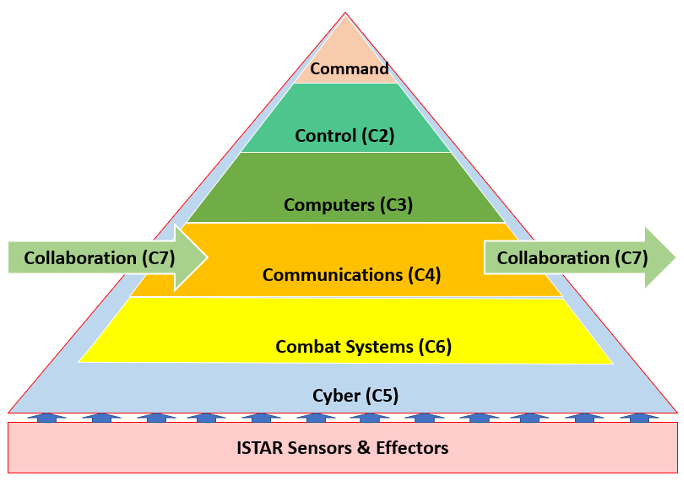
X-Factors: All of the discussion above has been mostly about physical infrastructure to enable C2. But these tools alone are powerless without guiding doctrine, principles, TTPs and talented people to cohese them into a combined capability. To enable post-digital C2, a myriad of X-factors need to be applied to the C6ISR model (see Figure 2). Converging the strengths of constituting components of the model into a single C2 System of Systems, cohesing and synthesizing data into Information and cohering all these diverse parts in a useful capability is essential. Add to that coordination and cooperation, using hyper-connected networks and hybrid multi-clouds will demand an entourage of highly capable talented individuals, who are natural digital natives, comfortable working in the engine room of the post-digital world.
C6ISR+X Factors Model

C7I & C7ISR: Collaboration and interoperability with partners and allies will be the keystone. Much like the post-digital gig-worker is engaged in hybrid work cooperatives with digital nomads to flex and prosecute business tasks, future military formations will be temporary, complex, dynamic multi-domain and integrated formations, which will form, morph and polymorph to persistently collaborate in multiple domains and dimensions in the post-digital battlespace. Larger partners will be traditional military allies engaged in traditional War eg NATO, but increasingly local civilian partners during MACA Ops will form part of the mix eg COVID Sp Force, whilst others collaborations will form where the objectives of Defence and others align e.g. Red Team Hackers. Collaborators in each mission will connect into/out of Defence at the C4 layer (see Figure 3). The C2 of these dynamic relationships will require both creative and secure boundary architectures.
C7ISTAR Model
Conclusion
We’ve got to stop fretting about our ability to operate in the Information Age, just accept we have missed that boat. But we are well ahead of the competition in the impending post-digital age and as demonstrated by my granddaughter, our young solider/officers are total naturals in this era. The problem is us, our reluctance to let go of the old, outdated industrial-age doctrine, thinking and technologies that hold us all back. I am part of the problem, I thought we could Architect the Information Age war but I’m now thinking this is even too late. If we are to honour the courage of those who fought and died with Capt Grenfell, we need to retire our digital lances, invert the pyramid and admit we all don’t know, trusting our young soldiers and officers to guide us to what the future will be and how we can enable it – but please, no “Peppa Pig”.

Martin Crilly
Martin Crilly is the Chief Architect & Engineering Authority to BAE Systems in the Middle East, and a Reserve Signals Officer. His background is in contempary ICT architecture, technology strategy, cyber-security, J2 and J6 with previous roles in BFC, ISS Ops Plans, GOSCC, DE&S Maritime and others. For more information and articles on Virtual War and similar topics, ‘follow’ him on Defence Connect.





